The Comprehensive Guide to Ethereum Staking Risks
Ethereum staking offers attractive rewards, but it's crucial to understand the potential risks involved. This definitive guide provides an in-depth analysis of all risk factors and mitigation strategies for both individual and institutional stakers.

Introduction to Ethereum Staking Risks
Ethereum's transition to Proof of Stake (PoS) has revolutionized how participants secure the network and earn rewards. Unlike mining, staking involves locking up ETH as collateral to validate transactions and create new blocks. While staking offers significant benefits—including energy efficiency and passive income—it also introduces unique risks that must be carefully considered.
This comprehensive guide examines the full spectrum of Ethereum staking risks, from technical and financial considerations to regulatory and protocol-level concerns. Whether you're a solo staker managing your own validator, using a staking service, or participating through an exchange, understanding these risks is essential for protecting your investment and maximizing returns.
We'll analyze each risk category in detail, provide real-world examples of staking incidents, and offer actionable mitigation strategies based on industry best practices. By the end of this guide, you'll have the knowledge to make informed decisions about your Ethereum staking strategy.


Slashing Risks: The Validator's Greatest Threat
Slashing is one of the most severe risks in Ethereum staking. It occurs when a validator violates the protocol rules, leading to a penalty that can include a portion or the entirety of the staked ETH being burned. Slashing serves as a critical security mechanism to discourage malicious behavior and maintain network integrity.
Types of Slashable Offenses
1. Double Signing (Equivocation)
This occurs when a validator signs two different blocks for the same slot. Double signing is typically caused by running the same validator keys on multiple machines simultaneously, often due to improper failover setup or key management errors.
2. Surround Voting
This happens when a validator signs two conflicting attestations where one "surrounds" the other in terms of the epochs they cover. This can occur due to client bugs, network partitioning, or intentional attacks.
3. Attestation Rule Violations
These include voting for conflicting checkpoints or other violations of the Casper FFG (Friendly Finality Gadget) rules that ensure consensus finality.
Slashing Penalty Structure
Slashing penalties in Ethereum follow a three-part structure designed to punish violations proportionally to their severity and impact on the network:
- Initial Penalty: A minimum of 1 ETH is immediately deducted from the validator's balance.
- Correlation Penalty: Additional penalties based on how many other validators are slashed within a specific timeframe. This can be severe if many validators are slashed simultaneously, potentially resulting in the loss of the entire 32 ETH stake.
- Ejection: The validator is forcibly removed from the active set and placed in an exit queue.
- Withdrawal Delay: A mandatory 36-day waiting period before remaining funds can be withdrawn.
The chart above illustrates the relative severity of different validator penalties. While offline penalties are relatively minor, slashing events like double signing and surround votes can result in significant financial losses.
The Medalla Testnet Incident
August 2020Background
During the Medalla testnet, a major slashing event occurred when Prysm clients experienced time synchronization issues due to a bug in the Cloudflare Roughtime service. This caused validators to attest to incorrect data, resulting in mass slashing.
Outcome
While this occurred on a testnet with no real ETH at stake, it demonstrated how a single point of failure in time synchronization could lead to widespread slashing events.
Key Lessons
- •Implement multiple time sources for validator nodes
- •Set up monitoring for time drift
- •Maintain client diversity to reduce correlated failures
- •Test failover systems thoroughly before implementing them
Financial Risks: Beyond Slashing
Beyond slashing, Ethereum stakers face several financial risks that can significantly impact returns and overall investment performance. These risks extend beyond protocol-level penalties and include market dynamics, opportunity costs, and liquidity constraints.
ETH Price Volatility
While staking generates rewards in ETH, the fiat value of these rewards fluctuates with ETH's market price. A significant price decline can offset or even exceed staking yields when measured in fiat terms. For example, a 5% annual staking yield would be negated by a 5% decrease in ETH price.
Risk Level: High
Liquidity Constraints
Staked ETH is subject to withdrawal restrictions. Solo stakers must wait through an exit queue when unstaking, which can take days or weeks depending on network conditions. This illiquidity represents an opportunity cost and prevents rapid response to market conditions.
Risk Level: Medium-High
Diminishing Returns
As more validators join the network, the staking reward rate decreases. When Ethereum staking first launched, annual percentage rates (APR) were above 10%. As of 2024, they have settled around 3-5% and may continue to decrease as participation grows.
Risk Level: Medium
Opportunity Cost
Capital allocated to staking cannot be deployed elsewhere in potentially higher-yielding investments. This opportunity cost becomes more significant during bull markets or when DeFi protocols offer substantially higher yields than staking.
Risk Level: Medium-High
Staking Returns vs. Risk Analysis
Different staking methods offer varying risk-reward profiles. The chart below visualizes the relationship between expected annual rewards, risk levels, and market share for various Ethereum staking approaches:
As shown in the chart, solo staking typically offers the highest rewards but comes with greater risk and technical complexity. Exchange staking provides lower returns but with reduced risk and minimal technical requirements. Pooled staking and liquid staking derivatives offer a middle ground, balancing decent returns with moderate risk levels.
Technical Risks: The Operational Challenges
Technical risks represent a significant challenge for Ethereum stakers, particularly for those running their own validator nodes. These risks stem from hardware failures, software bugs, network issues, and operational errors that can lead to penalties, reduced rewards, or in severe cases, slashing events.
Hardware Failure
Validator nodes require 24/7 uptime. Hardware failures can lead to downtime penalties and missed attestations.
Network Connectivity Issues
Unstable internet connections can cause missed attestations and proposals, resulting in penalties.
Client Software Bugs
Bugs in validator client software can lead to unexpected behavior and potential slashing events.
Key Management Errors
Improper handling of validator keys can lead to theft, loss, or accidental slashing.
Power Outages
Extended power outages without backup power solutions can lead to significant downtime penalties.
Misconfiguration
Incorrect validator setup or configuration can lead to poor performance or security vulnerabilities.
Validator Client Considerations
The choice of validator client software significantly impacts your technical risk profile. Each client has different features, security characteristics, and update frequencies. Running minority clients contributes to network health while potentially reducing your risk exposure to client-specific bugs.
| Client | Language | Resource Requirements | Update Frequency | Notable Features |
|---|---|---|---|---|
| Prysm | Go | Medium | High | User-friendly web UI, extensive documentation |
| Lighthouse | Rust | Low-Medium | Medium | Security-focused, efficient resource usage |
| Teku | Java | High | Medium | Enterprise-grade, high reliability |
| Nimbus | Nim | Very Low | Medium | Optimized for resource-constrained devices |
| Lodestar | TypeScript | Medium-High | Low | JavaScript ecosystem compatibility, research-oriented |
Technical Monitoring Best Practices
Implementing robust monitoring is essential for mitigating technical risks. A comprehensive monitoring setup should track validator performance, system health, and network conditions in real-time.
Essential Metrics to Monitor
- • Validator balance and rewards
- • Attestation effectiveness
- • Proposal success rate
- • System resource usage (CPU, RAM, disk)
- • Network connectivity and latency
- • Client synchronization status
- • System time accuracy
Recommended Monitoring Tools
- • Grafana + Prometheus
- • beaconcha.in validator monitoring
- • Alertmanager for notifications
- • Uptime Robot for external checks
- • Client-specific dashboards
- • Log aggregation systems
Alert Configuration
- • Missed attestations (>2 consecutive)
- • Validator offline status
- • Client out of sync (>60 seconds)
- • High system resource usage (>80%)
- • Disk space warnings (>80% full)
- • Network connectivity issues
- • Balance decreases beyond normal variance
Market Risks: Navigating Ethereum's Ecosystem
Market risks in Ethereum staking extend beyond simple price volatility to encompass broader ecosystem dynamics, competitive pressures, and evolving market structures. These risks can significantly impact long-term staking profitability and strategy.
Competitive Yield Pressure
As more validators join the Ethereum network, staking rewards naturally decrease. This competitive pressure creates a dynamic where staking yields must remain attractive relative to other investment opportunities to maintain network security.
Historical Staking Yield Trends
Ethereum staking yields have shown a clear downward trajectory since the Beacon Chain launch:
- • December 2020 (Launch): ~21.6% APR with limited validators
- • Mid-2021: ~7.5% APR as participation increased
- • Post-Merge (September 2022): ~5.5% APR with added MEV rewards
- • 2023 Average: ~4.2% APR with over 500,000 validators
- • 2024 Projection: ~3.5-4.0% APR as participation stabilizes
Liquid Staking Dominance
Liquid staking derivatives (LSDs) have captured a significant portion of the staking market, introducing new dynamics and potential centralization risks. As of 2024, liquid staking protocols like Lido, Rocket Pool, and Coinbase account for over 60% of all staked ETH.

This concentration creates market risks for all stakers, as large liquid staking providers could potentially influence protocol governance or create systemic vulnerabilities if they face operational issues.
MEV Market Dynamics
Maximal Extractable Value (MEV) has become an increasingly important component of validator rewards. Changes in MEV extraction methods, block builder competition, or protocol-level MEV solutions could significantly impact staking profitability.
Solo stakers who don't optimize for MEV extraction may find themselves at a competitive disadvantage compared to sophisticated staking operations that maximize these additional revenue streams.
Protocol Risks: Ethereum's Evolving Consensus
Protocol risks stem from the ongoing development and evolution of Ethereum itself. As a technology still in active development, Ethereum undergoes regular upgrades and changes that can impact stakers.
Upgrade and Fork Risks
Major protocol upgrades (hard forks) require validators to update their client software. Failure to upgrade in time can result in being on the wrong chain, missing attestations, and incurring penalties. The complexity of coordinating these upgrades across thousands of validators introduces systemic risk.
Upcoming Protocol Changes with Staking Impact
- EIP-4844 (Proto-Danksharding): Introduces blob transactions that may affect validator hardware requirements and block processing.
- Single Slot Finality: Could change validator duties and reward mechanisms to enable faster finality.
- Proposer-Builder Separation (PBS): Will formalize the relationship between block proposers and builders, potentially affecting MEV distribution.
- Verkle Trees: State data structure changes that may require significant client updates and potential migration processes.
Consensus Vulnerabilities
While Ethereum's Proof of Stake consensus mechanism has been extensively researched and tested, theoretical vulnerabilities or edge cases may still exist. These could include long-range attacks, nothing-at-stake problems, or unforeseen game-theoretic issues that might emerge under specific network conditions.
Ethereum Staking Risk Timeline
The highest risk period is during initial setup. Validator key mismanagement, client misconfiguration, and hardware issues can lead to immediate penalties or slashing events.
During the first few months, validators face a learning curve in maintaining uptime, monitoring performance, and responding to network changes or client updates.
Short-term stakers may experience higher reward variability due to luck in block proposals and network participation rates, potentially not matching expected APR calculations.
Regulatory Risks: Navigating Uncertain Waters
The regulatory landscape for cryptocurrency staking remains in flux globally, creating significant uncertainty for stakers. Different jurisdictions are developing varied approaches to staking regulation, taxation, and compliance requirements.
Securities Classification Concerns
In some jurisdictions, staking activities or staking services may be classified as securities offerings or investment contracts. The SEC's actions against certain staking services in the United States highlight this risk. Such classification could impose significant compliance burdens or restrictions on staking participants.
Tax Implications
Tax treatment of staking rewards varies widely by jurisdiction and continues to evolve. Key considerations include:
- Income vs. Capital Gains: Whether rewards are taxed as income when received or as capital gains when sold
- Taxable Events: When tax liability is triggered (block rewards, claiming rewards, selling rewards)
- Valuation Method: How the value of rewards is determined for tax purposes
- Record-keeping Requirements: Documentation needed to properly report staking activity


Client Diversity: A Network-Level Risk
Client diversity refers to the distribution of different validator client implementations across the Ethereum network. Insufficient client diversity represents a systemic risk to the entire network and, by extension, to all stakers regardless of which client they personally use.
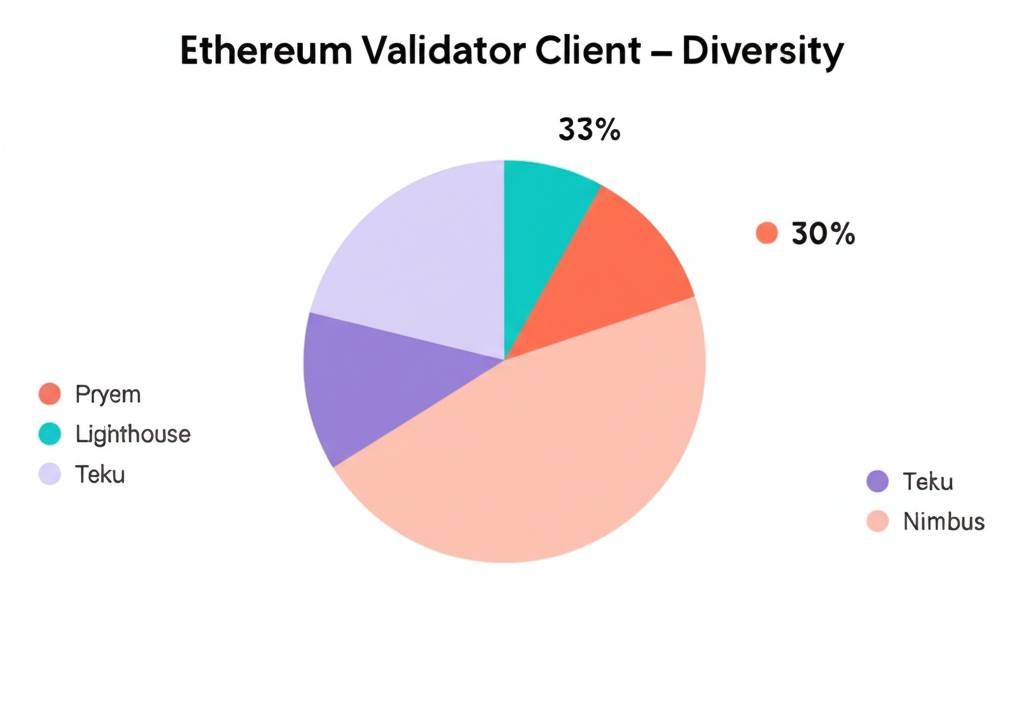
As of 2024, the Ethereum network still faces client diversity challenges, with Prysm maintaining a significant market share. This concentration creates a scenario where a critical bug in a dominant client could affect a large portion of the network simultaneously.
Supermajority Client Risks
If any single client implementation reaches a two-thirds supermajority of the network, it creates a scenario where a bug in that client could potentially cause the chain to finalize invalid states. This represents one of the most serious risks to Ethereum's security and could lead to catastrophic outcomes like chain splits or invalid finality.
Network Health Advisory: To improve network resilience, consider running minority clients like Nimbus, Teku, or Lodestar. If you're using Prysm, which currently has the largest market share, switching to an alternative client helps reduce systemic risk for all Ethereum stakers.
Historical Staking Incidents and Lessons
Examining past staking incidents provides valuable insights into real-world risks and effective mitigation strategies. While Ethereum's Proof of Stake has proven relatively robust, several notable incidents have occurred since its inception.
The chart above shows historical slashing events by quarter since Ethereum's Beacon Chain launch. Note the general downward trend as validator operators have improved their practices and client software has matured.
The Kraken Slashing Incident
February 2021Background
Kraken's staking service experienced a slashing event affecting 75 validators. The incident occurred due to a configuration error in their validator setup that caused double signing.
Outcome
Kraken covered all losses for affected customers, but the incident highlighted the risks of centralized staking services and the importance of proper redundancy configurations.
Key Lessons
- •Implement strict key management procedures
- •Test failover systems thoroughly in non-production environments
- •Consider the trade-offs between redundancy and slashing risks
- •Verify that high-availability setups don't create double-signing scenarios
The Lido Node Operator Incident
May 2022Background
A Lido node operator experienced slashing of multiple validators due to a misconfiguration during a planned migration between servers.
Outcome
The affected node operator was removed from Lido's set, and their insurance covered user losses. The incident led to improved operational guidelines for all Lido node operators.
Key Lessons
- •Develop clear migration procedures for validator transfers
- •Implement waiting periods between shutting down old validators and starting new ones
- •Use separate keys for each validator to limit the scope of potential incidents
- •Verify client configurations before going live
The Geth/Prysm Clock Drift Issue
November 2022Background
Many validators experienced missed attestations due to a time synchronization issue between Geth and Prysm clients after a network upgrade.
Outcome
While not a slashing event, affected validators experienced reduced rewards until client updates were released and implemented.
Key Lessons
- •Maintain multiple time sources
- •Monitor clock drift actively
- •Update clients promptly after network upgrades
- •Consider running execution and consensus clients from different development teams
Comprehensive Risk Mitigation Strategies
While Ethereum staking involves inherent risks, implementing robust mitigation strategies can significantly reduce your exposure. The following approaches address the full spectrum of staking risks.
Technical Risk Mitigation
- • Use minority clients to improve network diversity
- • Implement comprehensive monitoring and alerting
- • Maintain secure, air-gapped key generation
- • Use hardware security modules for withdrawal keys
- • Implement redundant internet connections
- • Use uninterruptible power supplies
- • Regularly update client software
- • Consider distributed validator technology
Financial Risk Mitigation
- • Diversify across multiple staking methods
- • Consider liquid staking for partial liquidity
- • Maintain a balanced crypto portfolio
- • Evaluate staking as part of overall investment strategy
- • Consider staking insurance products
- • Maintain detailed records for tax compliance
- • Regularly reassess yield vs. risk trade-offs
Protocol Risk Mitigation
- • Stay informed about upcoming protocol changes
- • Participate in testnets for major upgrades
- • Follow multiple information sources
- • Join validator community forums and discussions
- • Maintain client diversity in your validator setup
- • Consider gradual entry into staking
Regulatory Risk Mitigation
- • Consult with crypto-knowledgeable tax professionals
- • Maintain detailed records of all staking activities
- • Stay informed about regulatory developments
- • Consider jurisdictional diversification
- • Use compliant staking services when appropriate
- • Separate personal and business staking activities
Slashing Protection Strategies
Slashing protection deserves special attention as it addresses the most severe penalty risk in Ethereum staking. Modern validator clients include built-in slashing protection databases, but additional precautions are recommended:

- Never run the same validator keys on multiple machines simultaneously - This is the most common cause of slashing events
- Implement proper shutdown procedures - Always ensure validators are fully stopped before migrating to new hardware
- Backup slashing protection databases - These contain records of previously signed messages to prevent double signing
- Use import/export tools when migrating - Most clients provide tools to safely export and import validator data
- Implement waiting periods during migrations - Wait several epochs between shutting down old validators and starting new ones
Personalized Risk Assessment Framework
Before committing to Ethereum staking, conducting a thorough risk assessment based on your specific circumstances is essential. The following framework helps evaluate if staking aligns with your risk tolerance and technical capabilities.
Staking Risk Assessment Calculator
Risk Profile Analysis
Staking Method Comparison
Different staking methods offer varying risk-reward profiles. Understanding these differences is crucial for selecting the approach that best matches your risk tolerance and technical capabilities.
Risk Radar Analysis
The following radar chart provides a visual comparison of different risk categories across various staking methods. This multi-dimensional view helps identify which approach best aligns with your specific risk concerns.
Staking Insurance and Protection Options
As the Ethereum staking ecosystem matures, various insurance and protection options have emerged to help mitigate financial losses from slashing events, technical failures, or smart contract vulnerabilities.
| Insurance Type | Coverage | Typical Cost | Providers | Limitations |
|---|---|---|---|---|
| Slashing Insurance | Covers losses from slashing events | 5-10% of annual rewards | Nexus Mutual, Unslashed Finance | May not cover negligence or intentional violations |
| Smart Contract Coverage | Protects against smart contract bugs in staking protocols | 2.5-6% of covered amount annually | Nexus Mutual, InsurAce | Specific contracts must be covered; waiting periods apply |
| Staking Service Guarantees | Service provider covers slashing losses | Built into staking fees | Coinbase, Kraken, Bitcoin Suisse | Limited to specific providers; terms vary widely |
| Self-Insurance Pools | Community-based coverage for validators | Contribution-based | Rocket Pool, StakeWise | Limited coverage amounts; protocol-specific |
When evaluating insurance options, carefully review coverage terms, exclusions, and claim processes. Insurance should be considered as part of a comprehensive risk management strategy, not a replacement for proper operational security and best practices.
Conclusion: Balancing Risk and Reward
Ethereum staking represents a significant opportunity for passive income generation and network participation, but it comes with a complex risk landscape that requires careful consideration. By understanding the full spectrum of risks—from technical and financial to regulatory and protocol-level— stakers can make informed decisions and implement appropriate safeguards.
The most successful staking strategies balance risk mitigation with reward optimization. This often involves diversifying across staking methods, implementing robust technical safeguards, staying informed about protocol developments, and maintaining regulatory compliance.
As Ethereum continues to evolve, so too will the risk landscape for stakers. Remaining adaptable and continuing to educate yourself about emerging risks and best practices is essential for long-term staking success.
Key Takeaways
- Understand all risk categories before committing to staking
- Select a staking method that aligns with your risk tolerance and technical capabilities
- Implement comprehensive monitoring and security measures
- Diversify across staking methods when possible
- Stay informed about protocol changes and regulatory developments
- Consider insurance options for additional protection
- Contribute to network health by using minority clients
Learn More
- •Ethereum Staking Rewards Explained - How rewards are calculated and distributed to validators
- •Environmental Impact of Ethereum Staking - An in-depth look at the environmental benefits of Proof of Stake
- •Future of Ethereum Staking - Exploring upcoming developments in the Ethereum staking ecosystem
- •Ethereum Staking Security Best Practices - Comprehensive security guidelines for validators


